They Wanted to Scam G2A, But Things Didn’t Go Exactly as They Planned

Priestess Cassandra warned the Trojans not to bring the big wooden horse into the city. But who would listen to her, even were she not cursed by Apollo to be disbelieved? The horse made a great impression on the citizens of Troy, and it was, after all, a gift. Why should they turn away such a wonderful offering?
We all know this story, right? The Trojan horse symbolizes a deceitful gift which brings doom on the unwary souls. In the IT world, a trojan is a type of malware disguised as useful software or files, unwittingly installed by the users themselves. Sadly, not everyone pays heed to the ancient tale.
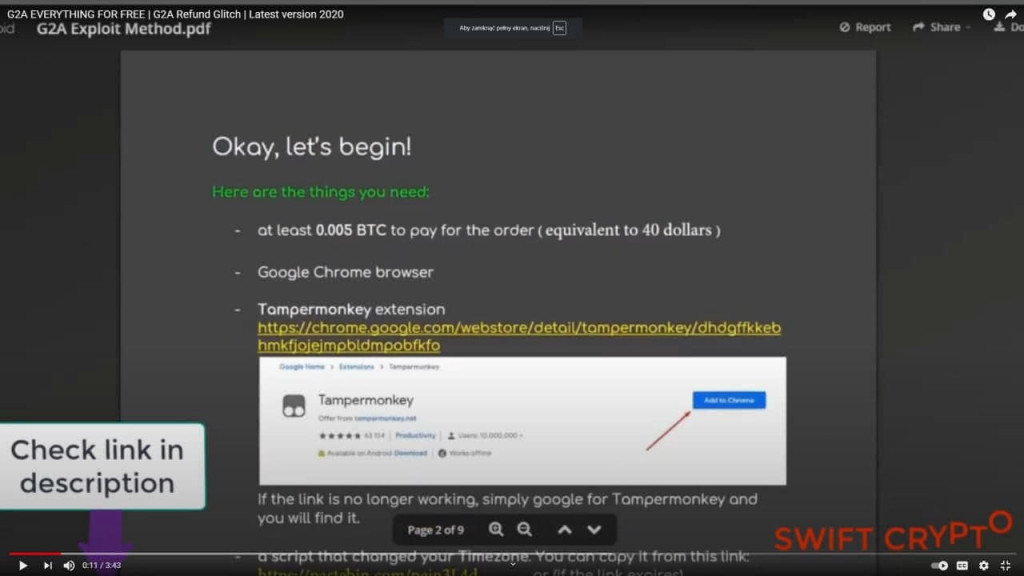
I work in the IT department at G2A — a popular marketplace for gamers. Not too long ago my team learned about some interesting YouTube videos. They claimed there was a vulnerability in our systems that customers could exploit to get game keys for free. All you needed to do was follow the instructions in the video and add a simple script. A teeny-weeny browser add-on. You know, just to help with the process a little bit.
Bring that horse in, you say? Maybe we should set it on fire instead?
I though everyone was familiar with the Trojan horse story, so people would be more careful. They weren’t. Normally, you have doubts, but it’s so easy to silence this little inner voice of reason. And the story sounds pretty legit, so why not try the trick for an easy win?
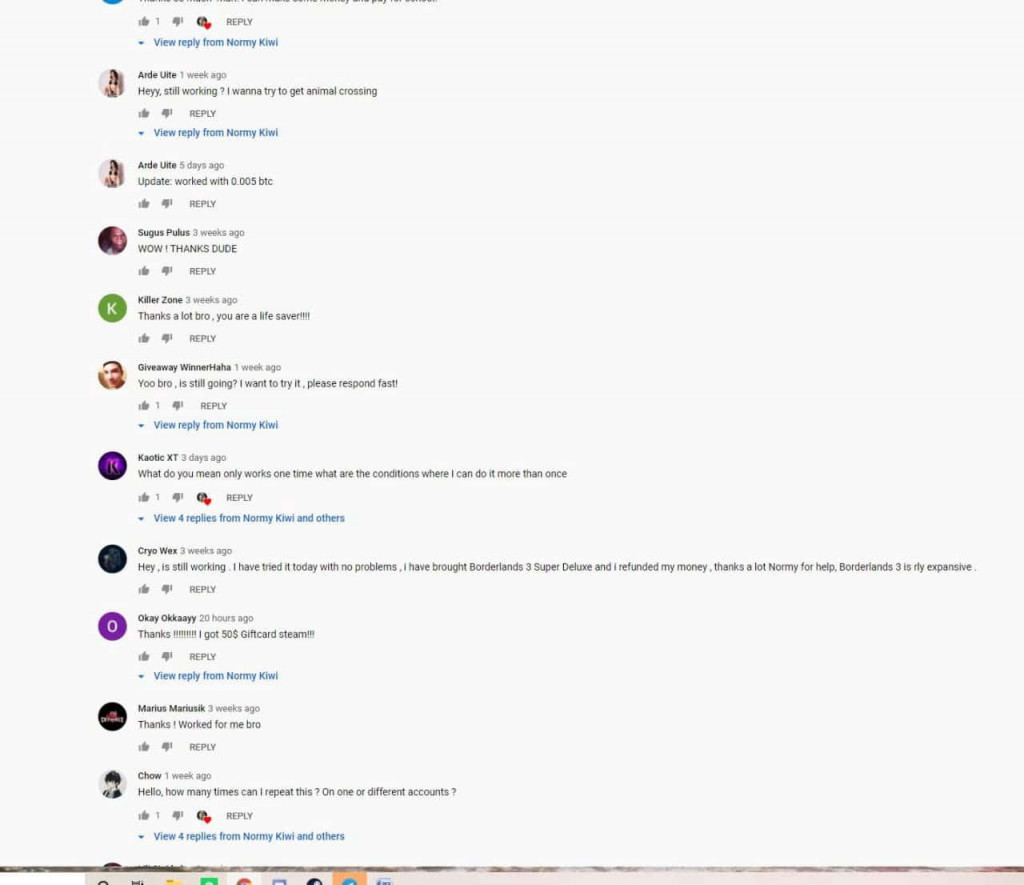
The video claimed that the vulnerability, called the time zone glitch, lies in the time differences and works only for bitcoin payments. All the user needs to do is change the system time to a far future date before completing the purchase. Then, with the help of a plugin called Tampermonkey and a wee innocent script, G2A servers will allow the transaction to proceed, but the bitcoin system will make a refund, detecting an error in time. As a result, the user will pay nothing. And G2A will send the game codes anyway! What a profit, right? Right?! The YouTube video even stated that G2A wouldn’t spot the fraud anyway, since they have such a large turnover, so there’s no need for users to worry. Heck, even the comments section is filled with at least a couple dozen claims that it works like a charm!
The horse is in Troy
And so the Trojans rejoice around the gift, celebrating a long-awaited victory over their enemies. The war is over, Achaeans are nowhere to be seen…
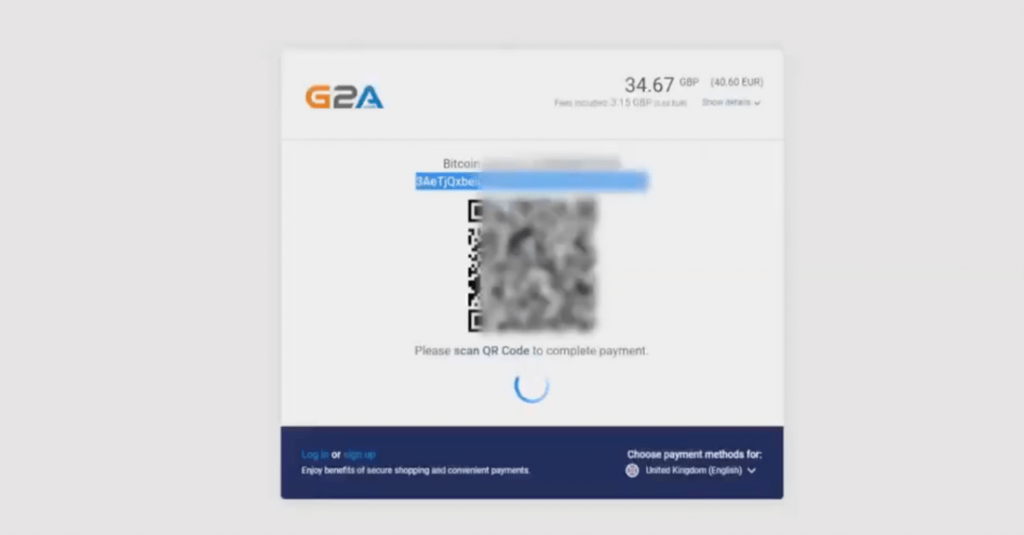
Tempted by the video, the user goes on to install the browser add-on and creates a bitcoin wallet. It’s difficult for me to believe that a user experienced in bitcoin payments would fall for this scam. Anyway, the poisonous script does two things. First, it displays a fake warning that a time discrepancy was detected. This is to make the user at ease. Then, just as the user enters the bitcoin wallet address for the payment, it smoothly replaces it with a different one. The address functions somewhat like a bank account number, so when the user completes the transaction, the money goes straight to the scammer.
As the night comes, Achaeans descend from the horse. They open the gates and soon looting, burning and murdering commences…
Well, perhaps this analogy might have gone a bit too far, but aside from losing money, it could have been worse. Much worse. A slightly different code could have entered the system and recorded sensitive data. Think passwords, bank account information, various details of browser sessions.
The Trojans had some opportunities to spot the deception.
Same goes for the users.
First, the scammers offered something for free, and as we know, nothing is free in this world. They want you to install their add-on, which is already a HUGE red flag. They also encourage the user to pay bigger amounts because this trick will only work once. Or so they say.
How does bitcoin help trojan makers?
With bitcoin, it’s oftentimes impossible to track who was involved in a transaction. The addresses used are not entirely anonymous, but they are generally used only once. If they are not associated with, say, a delivery address, they cannot be used for tracking purposes. This is why bitcoin was used for selling drugs on the Silk Road platform. That nasty place was of course shut down by the FBI in 2013, but bitcoins are still used in all kinds of ways on the deep dark web.
If the wallet address is used only once, it cannot be traced. Scammers need to update the code each time someone falls for the trick. They also upload new videos on a regular basis to prevent the unwanted negative comments.
Who fell for the Trojan horse?
It’s difficult for us here at G2A to assess how many people used the script so far. These people wouldn’t come forward and let us know anyway since they were trying to cheat us, after all. This doesn’t have any impact on us, but it does help the scammers — the folks who fell for their tricks possess a sense of guilt and won’t disclose any details to the authorities. Why? Because they would have to admit that they became victims while trying to commit fraud themselves.
The scam uses bitcoins as a currency and newcomers are easy to fool, since they are less likely aware of how cryptocurrencies work. It is relatively easy to create a bitcoin wallet and the process does not require any documents. There are a lot of online platforms where you can buy cryptocurrency. You can even get it in some ATMs!
Even at this point we don’t know who’s behind the refund scam. The videos are deleted, then uploaded again and commented on by bots. You know what’s the best thing to do if you see such a clip? Simply click Report and save gullible users a massive headache.
What can we do to help?
While we do our best to secure our systems, we have no way of preventing our clients from the harm they cause themselves by installing software from suspicious sources. They do that on their own risk. The only thing we can do is warm them and by that, help prevent this kind of damage.
Why do I care if the people who were scammed tried to steal from G2A in the first place? I don’t really think of it like that. Like I mentioned above, the same script could have been much more destructive. Someone could have gained access to even more sensitive data and downloaded more malicious software somewhere in the background. With more sophisticated technology, such as AI-run household appliances and autonomous cars, viruses and trojans will become more and more dangerous. We need to be more vigilant. That’s why it’s important to spread awareness and help one another.
Also, we really, really do not like the idea of our platform being used for such a sinister purpose. G2A is all about getting good deals on video game stuff and having fun.
Of course, there is no such thing as impenetrable fortresses and G2A is no exception here. Errors and bugs do happen and they can be used against us too. I would even prefer that a person who found a glitch or fell victim to a scam informed us. We would repay them greatly. And everyone benefits from that.To end on a mythological note, the main constructor of the horse was Epeius, known for his cowardice. After the horse was drawn into the city and the night fell, he was afraid of being discovered by the Trojans and did not want to exit first. This perhaps is something to keep in mind when you happen across a similar scamming tactic.
by Marek Pokrywka, IT Lead at G2A.COM